The Rise of the Fake Email: How to Identify and Protect Yourself
Before we understand the harms of fake emails, it's important to be able to identify one when you see it in your inbox.
A fake email basically refers to forged or fraudulent emails that are sent with the aim of deceiving the recipient.
The purpose varies greatly according to each type of fake email, and can seek out personal and confidential information for financial scams, install malware (viruses) on the recipient's device or even direct them to fake websites to buy products at strangely attractive prices.
How to spot a fake email?
Every fake email has some fundamental characteristics which, if properly observed, will protect you from becoming a victim of some kind of scam. Let's take a look:
- Suspicious sender: check that the sender's name has no strange characters or spelling mistakes.
- Unofficial emails: be wary of email senders who don't use official domains (such as 'gmail.com', or different spellings, such as 'SafetiMaills.com' - 'Instead of SafetyMails.com', or 'SafetyMails.Superdesconto.com';
- Inappropriate requests: emails should never ask for personal data, such as passwords, credit card numbers or bank details, among others;
- Spelling: it seems obvious, but fraudulent emails don't usually value the quality of their spelling. They usually have gross errors in the subject line or the sender's name, for example;
- Shortened links: hyperlinks that use shortening services (such as bit.ly) may be masking the final destination. Don't click.
- Masked links: many hyperlinks are placed over words (where you can't see the full URL). To make it easier, just hover the mouse pointer over the hyperlink and that's it: you'll see the destination URL displayed and you'll know if it's reliable or not.
- Urgency: emails that ask for action to be taken immediately, as a matter of urgency, are suspicious;
- Attachments: emails with attachments can be dangerous. Government agencies, especially tax authorities and e-commerce stores, never send emails with attachments. Don't open this type of file, except in cases where the sender is well known and trustworthy.
- Unrealistic promises: you know that $1,800 product being offered in a 'special batch' for $400? Run away!
- Design and formatting: these types of emails usually have poor layouts, with low-quality images, often trying to look like some famous website.
Master tips for identifying a fake email
Here are 2 more infallible tips, but they will require a little more skill and technical knowledge to spot a fake email.
Date of publication of the site: many fake sales sites, which promise products at over-inviting prices, are created just for the purpose of the scam and are then abandoned. They sell and never get back to you. So be extremely wary of sites that have been published too recently.
And how do you know?
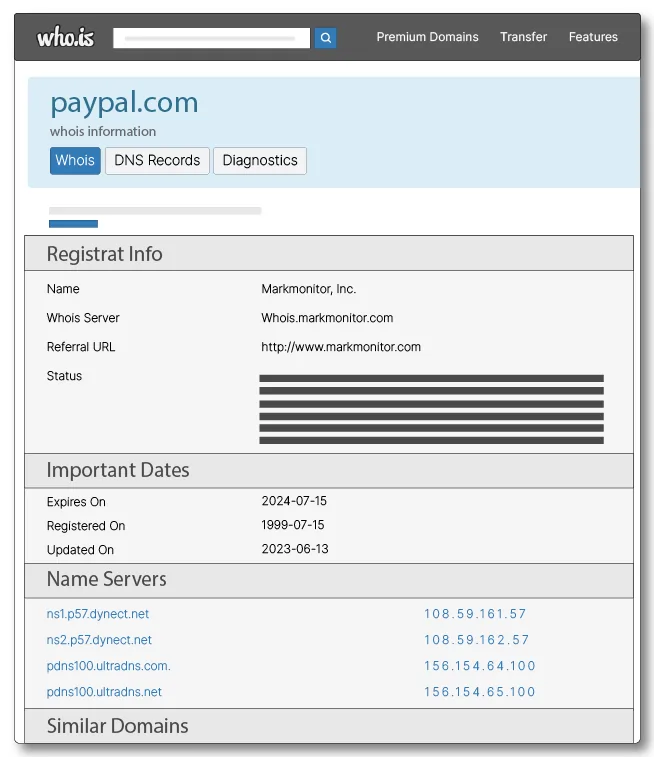
For sites in Brazil (.com.br), go to https://registro.br/tecnologia/ferramentas/whois/. For sites on other domains, go to https://who.is/.
Type in the domain to be searched and see the results.
Email authentications: in order to be sent and received by email providers, messages need to go through certain security authentications, such as SPF, DKIM and DMARC.
You can find out, using any webmail, whether these authentications are functional and appropriate in an email.
In Gmail, for example, just open the message and look for the 'plus' icon (the one with the 3 dots) and look in the menu for the option '<> Show original'.
Obviously, each webmail will have its own way of identifying whether authentications are working. But knowing this is already a golden tip, isn't it?
Types of fake email
Now that you know how to identify a fake email and how to avoid it, it's time to find out about the most common types of fake email you can find in your inbox.
Phishing
These are messages made to look like emails sent from a legitimate source, such as a bank or an e-commerce or technology company. The aim is to obtain personal information such as passwords or credit card numbers.
In many cases, this fake email is supplemented with data obtained publicly from the recipient (such as the person's name, the company where they work and their job title, for example, which can easily be obtained from social networks), in order to give the message greater credibility.
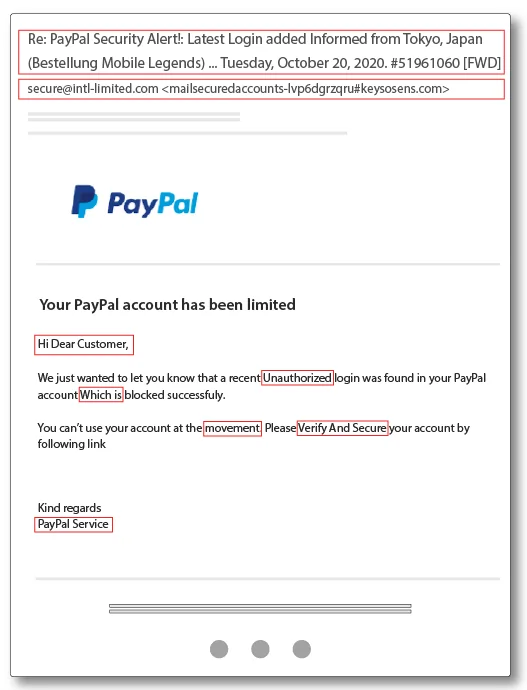
Whaling
This is a more elaborate type of phishing, aimed at high-profile people, such as executives or decision-makers in companies. This type of fake email tries to talk about legal or critical executive issues, demanding an immediate response.
Examples include messages about overdue taxes, federal revenue, extrajudicial notices, among others.
Scam
This fake email aims to defraud recipients by convincing them to send money or access links that lead to false offers. Usually, after a first approach, when the recipient replies, the fraudster starts talking about opportunities and asks for money to start some process or procedure that will generate a large sum of money as a reward.
Malware
If we're going to talk about a type of fake email that is extremely harmful, here it is: these emails involve sending mass messages with links that, once clicked, install malicious software that can, among other things:
- record, through a keylogger, all the keystrokes made in order to steal confidential information (such as email passwords, bank passwords, etc.);
- installation of ransomware, which is a type of software that encrypts files on the recipient's device (PC, notebook, smartphone, tablet, etc.) and demands a ransom for their release.
SPAM
Perhaps the least harmful type of fake email, spam emails involve sending unsolicited messages in bulk, usually for advertising purposes, to recipients who have not asked to receive them.
However, there are cases of spam that contain malware or phishing techniques. Staying vigilant is essential.
Each type of fake email has its own characteristics and methods, but they all share the objective of deceiving the recipient.
Are disposable emails fake emails?
As a rule, disposable emails (or temporary emails) are not fake emails, as their primary purpose is to give the user the possibility of having an email account for a short period of time before being discarded or deleted.
The objectives of this type of email include:
- Temporary: they are configured to exist only for a period of time
- Anonymous: you don't know who the person behind that email address is, and it doesn't require any personal information to create it.
- Convenient: they can be created quickly for immediate, one-time use
Common uses include:
- Testing services: used to sign up for online forums or environments where the email address is exposed;
- Preventing spam: used only once, they bypass traditional email verification processes and prevent future messages from being sent.
HOWEVER, this type of email can represent a danger and a channel for abuse, such as:
- Potential for abuse: they can be used inappropriately to bypass security checks, repeatedly sign up for services with offers limited to new users, or to send anonymous messages that could be malicious
- Fraud: using a fake email on an e-commerce site, together with a fake credit card, makes fraudulent purchases difficult or impossible to trace.
Tip for companies that want to avoid disposable email sign-ups
If you want to avoid disposable emails, temporary emails or fake emails when registering for landing pages, websites, etc., use SafetyMails' real-time email verification API.
Open a free account now and try out the features!
Avoid bounces
Upload and verify more than 2 million email addresses at once: If you deal with large email lists,
it is extremely important to check them frequently.
Damage caused by fake emails to companies
In addition to the damage that fake emails cause to individuals, companies also suffer from the actions of this type of malicious message, on many levels.
Starting with financial losses, inattentive employees can end up paying illegitimate invoices, as in the case below, where a fraudster tries to impersonate registro.br:
The sender of the email is clearly trying to impersonate registro.br and demanding an annual fee for an Internet domain.
Points to note
- the layout of the email is clearly not from registro.br
- the amount of the supposed invoice is much higher than what is normally paid
- the due date is the same day as when the email was sent (requiring urgent payment)
- the sender has no chance of being real
The second damage is directly related to the company's reputation. A fake email can lead to the theft of personal data and sensitive personal data, encryption of databases, etc., leading to financial losses, the reporting of the data protection incident to the National Data Protection Authority, as well as having to publicize the incident.
In this way, the credibility of the business is shaken, eroding the relationship with current clients and causing obstacles in the relationship and compliance analysis of new clients. This kind of damage is extremely costly to recover from.
Depending on the size of the problem, this could even involve heavy fines from regulatory bodies, as well as possible legal costs.
The third problem can be considered a mixture of the first two, as it involves the interruption of operations. When a fake email results in a successful attack, it can compromise vital systems, which will need to be shut down to mitigate problems. This potential business interruption can lead to financial losses and damage to customer relations, as well as requiring additional operating costs.
For this reason, it is extremely important that companies are constantly working towards the maturity of their data protection and privacy policies and actions, with the adoption of protection software, technologies and practices, mapping of their suppliers, constant training of their teams in terms of awareness and safe practices (such as the clean desk policy, for example, access with separate levels, control of mobile devices, protected networks, etc).
Fake emails and elections: a threat to democracies
During elections, the integrity and transparency of the process are essential. After all, we are talking about the future of a nation.
When society talks about 'fake news', it is often closely associated in people's minds with social networks and messaging apps such as Whatsapp and Telegram. However, SMS, email and even leafleting are channels through which this type of practice can be carried out.
In the digital sphere, fake email can be a highly destructive tool when it comes to elections. It is a way of distributing false information uncontrollably to a very specific target group, since it is possible not only to know who will be targeted, but also to monitor each person's behavior in relation to this content.
Among the harms of fake emails in electoral processes, we can mention:
- Dissemination of disinformation: malicious politicians or candidates and their advisors can spread false information about opponents, from false accusations to skewed election poll results, incorrect information about polling places, etc.
- Manipulation of public opinion: sending this type of fake email with derogatory or false information about people or electoral polls, spreading conspiracy theories, can influence recipients to alter their perception of their candidates, leading to a change in voting intention and even discrediting the electoral process as a whole.
- Impact on electoral results: the impact of these fake emails can be so profound that they can end up altering the course of an election, discouraging voter participation and affecting turnout.
Fighting Fake Email: emerging technologies
Obviously, the market is not turning a blind eye to this whole threatening scenario. Quite the opposite. Fake email is a phenomenon that has been closely monitored for decades and many security measures have been adopted.
Let's take a look at some of them:
- Robust authentication systems: DMARC, DKIM, and SPF, which are email security protocols that help verify that senders are who they say they are and ensure that emails have not been altered in transit;
- Advanced email filters: there are filters based on contextual analysis, analyzing who sends, when, how and how often, and what the recipient's behavior is with these emails. In addition, there are behavioral filters, tracking recipient actions (such as reporting an email as spam or deleting it unread), helping the provider's algorithm to improve its protections against phishing;
- Artificial intelligence: systems that are becoming capable of creating advanced fake email investigation algorithms that analyze the text of emails for signs such as exaggerated urgency, typical grammatical errors and other indicators of fraud;
Key measures against fake emails: training and information
Technologies are there to make people's lives easier, that's a fact. But it can't do all the work. Human intelligence must be the most important factor in the decision-making process.
That's why digital education is a powerful defense tool against the growing number of fake emails.
In schools
From an early age, pupils are introduced to a universe that is now basically digital: smartphones, social networks, online shopping, digital cards, proximity payments.
They need to be educated about internet safety from an early age. And this doesn't just mean talking about the popular antivirus, but also about taking care when registering and using passwords, using their fingerprints, being careful when accessing certain types of websites, etc.
Here, it's even more important to emphasize security against fake emails, since young people are so connected to social networks that they end up imagining that email is an outdated technology, whereas it is extremely useful and in demand, especially in life as an active consumer and in professional adult life.
In companies
From the moment they are hired, employees must be instructed and introduced to the reality of privacy and data protection, including with regard to the use of their email accounts, whether professional or personal, protecting the company's infrastructure against fake emails and the damage they cause.
To create a culture of security:
Install anti-malware: on all company assets
Workshops and webinars: there could be e-learning environments with the most basic content on information security and company policies, followed by recurrent face-to-face or distance training for all team members on an annual basis as a way of refreshing;
Adoption of clear privacy, data protection and information security policies: official documents containing all the company's guidelines for avoiding problems and setting parameters for what should be done in the event of doubts or incidents, with the knowledge of all employees;
Checklist against Fake Email
With your day-to-day practicality in mind, we've put together this brief checklist for you to use whenever you consider it necessary. Use it in your lectures, trainings and wherever else you want.
| Warning Score: 0 | |||
| About the sender | |||
| Is it known? |
|
If not, investigate | |
| Content | |||
| Any grammatical errors? |
|
If yes, be careful | |
| Does it have an exacerbated sense of urgency? |
|
If yes, be careful | |
| When you hover over links, do they look strange to you? |
|
If yes, be careful | |
| Is the domain that appears on the links different from the one on the sender? |
|
If yes, be careful | |
| Attachments | |||
| Does the email have attachments? |
|
If yes, make sure the sender is known! | |
| Was the email attachment requested? |
|
If not, don't open the attachment | |
| Security | |||
| Do you have anti-malware (antivirus) installed? |
|
If not, avoid opening attachments | |
| Have you checked SPF, DKIM and DMARC? |
|
If not, check if you still have doubts about the sender | |
| After all that, do you still have doubts? |
|
If so, try to use alternative means of confirmation, such as a whatsapp message or a phone call (if you know him/her). | |
| Warning Score: 0 | |||
Using technologies such as anti-spam, best practices, artificial intelligence, user training and continuing digital education for people, teaching about fake email and promoting better policies to protect personal and business information.
