mail masking is a practice used by people who want to keep their email accounts secret.
With the increase in online threats (such as hacking and theft of accounts and passwords) and, in particular, spam messages such as phishing, spoofing, scams and malware, it has never been more necessary to use privacy protection tools to protect users’ identities and guarantee the security of online communications.
This is why various types of practices are used in this regard, such as temporary emails (or disposable emails, burner emails), among others.
Table of contents
What is email masking
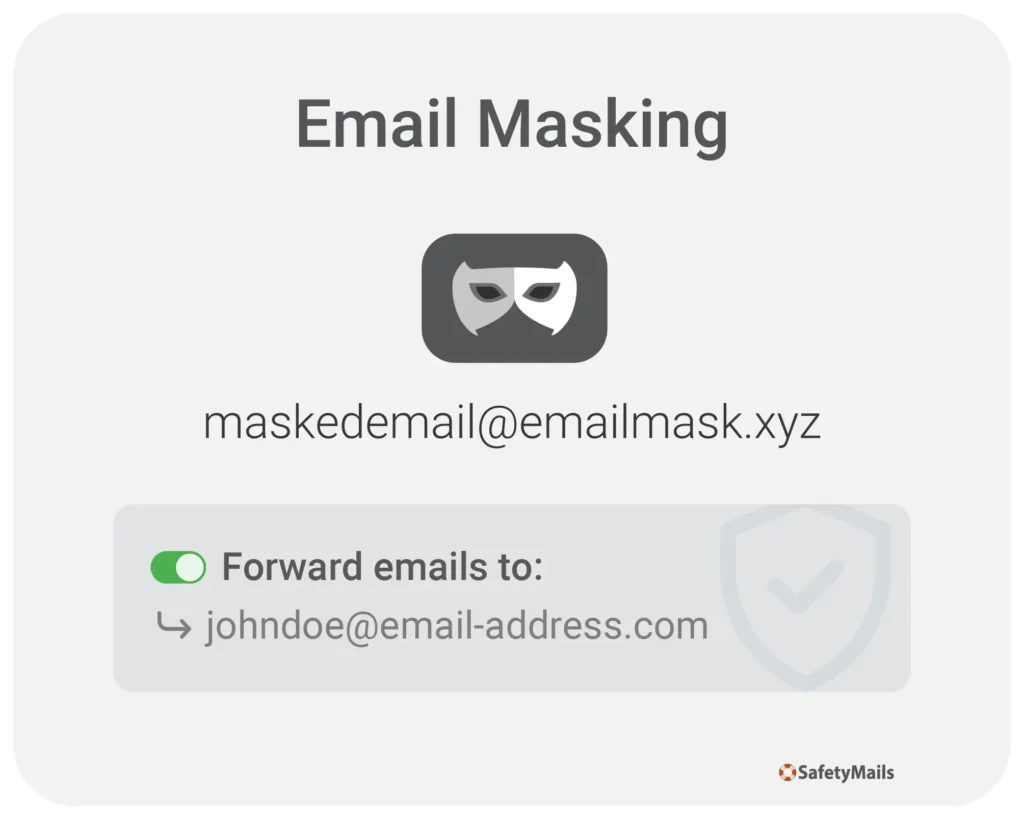
Put quite simply, it’s the practice of changing the appearance of your real email address using a mask, while keeping your real email account confidential.
Therefore, the user’s real email address is hidden and replaced with a temporary or alternative address.
The aim of this type of practice is to maintain the secrecy of the user’s real email address, preventing them from being targeted by spammers, but with the benefits of maintaining the use of their own email account for receiving and storing email messages.
How email masking works
This is basically a type of service offered by platforms specializing in online security and privacy, which provide an email forwarding service.
There are numerous online platforms for masked email services, usually offered by online security companies or virtual private network (VPN) services.
Unlike temporary email services, which are usually free and require no registration, the use of masked email requires registration and payment for the service.
With most services, all you have to do is create an account, access the platform, click on “New email mask” and follow the instructions, such as informing the (real) email to which the messages will be forwarded.
It is possible to make other types of settings, such as creating more than one masking for the same email address, programming the validity of a masking for discarding, among other possibilities.
What is the difference between email masking and email alias?
Although both practices are very similar, we can point out some subtle differences between them.
Email aliases are more permanent in nature and can be carried out by the user’s own email service provider, without the need for a third-party tool. Its name is chosen by the user, who defines which one will be used. It only allows messages to be received, not sent. This is the option with the greatest focus on message management.
With a more temporary profile, email masking is usually offered by cyber security services, with a randomly generated name. It allows messages to be sent and focuses more on privacy.
| Email Masking | Email Alias |
|---|---|
| Made from a third-party service | Made in the email service itself |
| Random name given by the service | Name chosen by the user |
| In addition to the name, uses a different domain | Uses the same domain as the user |
| More temporary in nature | More permanent |
| Focus on privacy | Focus on message management |
| Can send messages | Only receives messages |
Most common uses of email masking
- Marketplaces: negotiations in marketplaces that require the exchange of email messages between the parties. If the email address is made publicly available, it could be the target of email scraping and end up on spam lists. The use of masked emails protects the original email address.
- Security concerns: whenever sharing your email address seems risky, a masked email can be an excellent alternative (or even a burner email).
- One-off purchases on foreign websites: if you’re buying something on a website you don’t visit often, especially if it’s foreign and not subject to data protection laws, you could consider using a masking or burner email to carry out your operation.
Benefits of email masking
- Privacy protection: as the email address created in these services does not share the domain of the real email, there is no risk of privacy being breached.
- Protection against login and password theft: the risk of theft of login and password access to email accounts is greatly reduced, as the original email is kept confidential and the masking (as well as the alias) can be replaced.
- Protection against data sharing and spam: this type of service allows an email address to be quickly abandoned and replaced, preventing the receipt of spam messages and unauthorized data sharing.
Cautions when using email masking
Due to a greater awareness of privacy, people are choosing to use this and other services. However, like many practices that involve secrecy, these emails have also had their purpose diverted to reprehensible or questionable practices.
One example of this is their use for scams and fraud, precisely because of their temporary and confidential nature.
For this reason, companies are already monitoring and seeking to block the use of email addresses of this nature in their registration forms – which would be a setback for legitimate users of this type of service.
When choosing to use a masked email service, look for companies that are well-established, well-known and truly committed to security.
Impact of Masked Email on Digital Marketing
The use of masked emails can impact digital marketing strategies and data collection by companies. This is because many of these email addresses can be discarded and become hard bounces in contact lists, leading to reputational damage in email marketing.
For this reason, the digital market has adopted measures to prevent the use of these emails in its registration forms, such as:
- Email tokens instead of passwords: instead of passwords, the site sends a one-time use code by email. If the email no longer exists, the user cannot access the service and history associated with the account.
- Protection against registrations: forms with a real-time email checker, which prevents registrations made with temporary or disposable emails.
Conclusion
Email masking is a practice that can be used by those seeking greater privacy and security in their online communications.
By hiding the real email address, this technique aims to protect users from spam, phishing and other cyber threats.
Although it shares some similarities with email alias, it stands out for its emphasis on protecting the user’s identity and for allowing the creation of temporary, disposable addresses. However, its use must be done consciously and responsibly, considering the potential negative implications, such as misuse for fraud and scams.
Therefore, for its best use, companies and individuals should opt for reliable masking services to guarantee the security and effectiveness of this tool.
FAQ
What is email masking and how does it work?
It is a technique used to hide the user’s real email address, replacing it with a mask that alters its appearance (both in name and domain). This process is usually offered by platforms specializing in online security, which redirect incoming emails to the user’s real address, keeping their identity protected.
What are the main benefits of email masking?
Some of the benefits include privacy protection, security against login and password theft, and a reduction in spam. In addition, it allows users to quickly abandon a masked address in case of need, avoiding exposing their real email to malicious practices.
What is the difference between email masking and email alias?
Apart from the syntax (alias is a name chosen by the user in their domain and masking is a random address that is totally different from the original), email masking is focused on protecting the user’s privacy and security, while email alias is used mainly for organizing and managing communications.
What are the most common uses of email masking?
It is commonly used in situations that require greater secrecy and security, such as negotiations in marketplaces, one-off purchases on foreign websites, and when there are security concerns when sharing an email address. It helps protect users from practices such as email scraping and spam.
How can email masking impact digital marketing?
The use of masked emails can negatively affect companies’ digital marketing strategies, as many of these addresses are discarded, resulting in hard bounces from contact lists. This can damage the sender’s reputation and reduce the effectiveness of email marketing campaigns. For this reason, many companies are implementing measures to avoid using temporary or masked emails in their registration forms.



